The basic working principle of POS
I. Discussion
Hi everyone! I have seen a lot of dry goods about accounting, accounting, clearing, and reconciliation. I will share with you the basic working principle of the offline payment acceptance terminal-POS. In recent years, POS has also been continuously updated. Here, we will share the general abilities. If there are inaccuracies, please correct me.
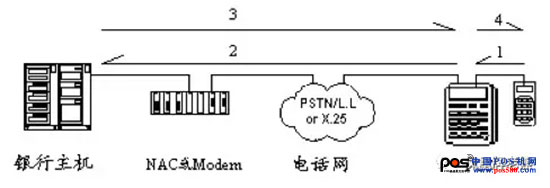
POS (point of sale) is a kind of terminal, a device attached to a computer. The terminal itself does not process the program and information, but sends the collected information to the host, which is processed by the host, and then reflects the result of the host processing.
1. POS trading This is a procedural concept that describes the process as follows:
Select a transaction (consumption, cash withdrawal, change of secret, etc.) at the POS, then swipe the card, insert the transaction amount, the cardholder password and other information requested by the POS prompt, and the POS will concentrate the data (package). Sent to the host in some way.
After receiving the information, the host decomposes it into its original independent information (unpacking), hands it to the accounting processor for processing, and then processes the result (mainly a return code, sometimes with a handling fee, authorization code, etc.) Information) repackaged and sent back to the POS;
After the POS receives the return information, it unpacks it and processes it accordingly (display, print, record POS, etc.)
The above three parts are closely combined. If any part is not completed successfully, it cannot be regarded as a complete transaction. May be "communication failed", "POS error", "host error" or "database error".
2. The successful host returns a "successful" return code (usually "00") and may have some additional information. For example: the query should return the balance; the authorization should return the authorization code, and sometimes there is a “partial approval amount†(for example, if you want to take 10,000 yuan, but the balance on the card is 5,000 yuan, the overdraft limit is 2,000 yuan, which is “partial approval amountâ€) Sometimes consumption or withdrawals will also return an authorization code.
3. The transaction failed. The host return code is not "00". The return code represents the reason for the transaction failure. For example: "55" - cardholder password does not match, "03" - merchant number is wrong, "23" - insufficient balance, and so on.
4. Account Processing Program The program that operates on the account database in the bank host. This part of the program will actually process the data sent by the POS: check whether the credit card has expired, whether the card password is met, and deduct the money from the cardholder's account to enter the liquidation process.
5. The front-end machine is in the old banking system. After the transaction data is sent to the bank, it goes directly to the host. All the processing (determining the legality of the personal password, judging the POS legality, accounting processing, etc.) is handled by the host. In the new architecture, the front-end machine is set up before the bank host, mainly to deal with the legality and other content, so as to ensure that the data sent to the bank host is legal, reduce the burden on the host, and run the program of the management terminal equipment (POS, ATM). .
6. The automatic rushing data is received by the host, and the host has processed it accordingly, but the return code does not receive the return information for various reasons (power failure, line fault). In this way, the POS cannot know the result of the host, so it will send a positive call to the host, the host will invalidate the corresponding transaction, and return a message to tell the POS to complete the correction. There are two specific implementations: 1. If a transaction does not receive a return message, it will continue to be positive until it succeeds. 2. If you do not receive the return message, you can press the “Cancel†button to return to the main menu. At this time, you can make some offline transactions (such as IC card), so the latter has more advantages.
7. The POS flow is the “POS flow accountâ€. The POS completes a successful transaction (ie, causing a change in the amount in the bank account, such as: consumption, withdrawals, deposits, transfers), and such transactions must ensure that no errors occur. To do this, record the contents of the transaction (card number, amount, etc.) in the POS, in case of checking with the host at the time of settlement, or for manual inquiry.
8. POS settlement is generally carried out at the “end of the dayâ€. The main purpose is to check the transfer transactions made by POS on this day with the records on the host, and then delete the records in the POS flow for the next day. use. At the time of settlement, the total amount and total number of POS transactions are generally checked. If one of the total POS amount and the total number of POSs is different from the host, the host returns “checking the unevennessâ€, and the POS must perform “batch-upâ€, although this Can not check all the errors, but under the guarantee of automatic measures such as automatic correction, the probability of error in settlement is quite low, just the total amount and the total number of pens are the same, the probability is lower. You may feel that it is safer to send all the transactions at the time of the daily POS settlement. However, this method is not very practical. The transaction volume of the POS will be very large, and the experience will be poor when the batch is sent for a long time.
9. When the batch is sent to the settlement check, the POS will send the water to the host one by one, and the host will check it one by one, and then the POS can delete the POS flow. Online transactions cannot be made until the end of the batch delivery. Generally speaking, the amount recorded by the POS is the actual transaction amount. It is impossible to modify it manually. Although the data on the host has various measures to ensure the correctness of the data, it is impossible to be absolutely correct, and the database may be artificially modified. Therefore, when checking data and batch delivery, most of the POS data will prevail. However, it is safer to record the transaction that the POS and the host cannot match in a database, and then wait for the merchant to send the printed ticket back, and then manually check it.
10. Communication Protocol Synchronous Communication Protocol and Asynchronous Communication Protocol Generally speaking, the POS can be synchronized, and asynchronously means that these two communication protocols can be used. We know that data communication is the transmission and reception of digital signals between two communicators. Suppose you send the following string of data: 12,23,34,45,56,67,78,89 To receive the data correctly, the receiver must know when the data begins and when it ends. Otherwise the signal will be mistaken. For the synchronous communication protocol, the sender sends a special electrical signal before sending the data, so that the receiver is ready to receive the data, and then the sender sends the above data continuously, all the transmission is completed, and then another special electrical signal is sent. End. For the asynchronous communication protocol, the sender sends a "start" flag before sending a value, and an "end" flag is sent at the end of each value transmission.
11. 8583 Data format The string data sent by the sender, how can the receiver know which part is the card number and which part is the transaction amount. Therefore, the communication parties must agree, for example: the first 16 data is the card number, then the 8 values ​​are the password ••••••, of course, the 8583 data format is not so simple, it is a complex data combination. The 8583 data format is an international standard that stipulates that certain data of financial transactions must appear in the data packet, but some data may or may not appear; some parts of the data packet are specified for certain data use, but There are many other uses that can be defined by themselves.
12. Packing and unpacking various data (card number, password, etc.) is originally stored in a distributed manner. Before sending, these scattered data must be combined into a series of consecutive data strings according to the data format. This is the packing. After receiving continuous data, to use a certain data, this data must be separated from the data packet according to the data format. This is unpacking.
13. Network Controller NAC
There are two main manufacturers of network controllers: Hypercom in Australia and Ruibo Technology in Hong Kong. The network controller of Ruibo Technology is similar to Modem. Each board corresponds to a downlink port (connected to the POS by telephone line) and an uplink port (connected to the host computer by serial port). This kind of network controller is used less in the market. The market mainly uses Hypercom's NAC6/16. Its uplink (connected to the host) generally has only one (one uplink board), and the maximum expansion to two upstream boards is sufficient, and more than a dozen downstream boards can be managed. The telephone line is connected to the POS). This can save the host's port, and at the same time allow more than a dozen POS to communicate with the downstream board, so that dialing is always busy, improving the efficiency of the POS system.
14. The cardholder password is usually 6 digits (plain text). The password is sent to the bank host kernel pair. During the password transmission process, the password cannot be obtained by other people. Therefore, the password must be kept in the form of ciphertext after the password is entered, even if the bank check password is the password ciphertext. The POS uses a bank card, and the cardholder enters the password plaintext on the password keyboard. The data from the password keyboard is the encrypted password ciphertext data, so that even if the password is intercepted during the password transmission process, the password plaintext cannot be obtained.
15. Encryption and Key Cryptography The method of converting plain text into ciphertext is the secret key. The protection key is not known to others. The POS generally places the key in the password keyboard. The password keyboard has a boot self-destruct function. When the person attempting to obtain the key opens the password keyboard case, the key is automatically lost.
Garden Umbrella,Garden Parasol,Cantilever Parasol,Patio Table Umbrella
Shaoxing Shangyu Sansan Umbrella Co., Ltd , http://www.sansan33.com